Why should we care about SSDLC in application security?
Due to its globally accessible nature, applications are becoming more popular targets for attackers to compromise an organization’s security
SSDLC or Secure Software Development Lifecycle is structured to deploying secure software applications has become increasingly important due to the rise in security risks.
Software application are designed and developed with functionality first in mind and security as a distant second or third
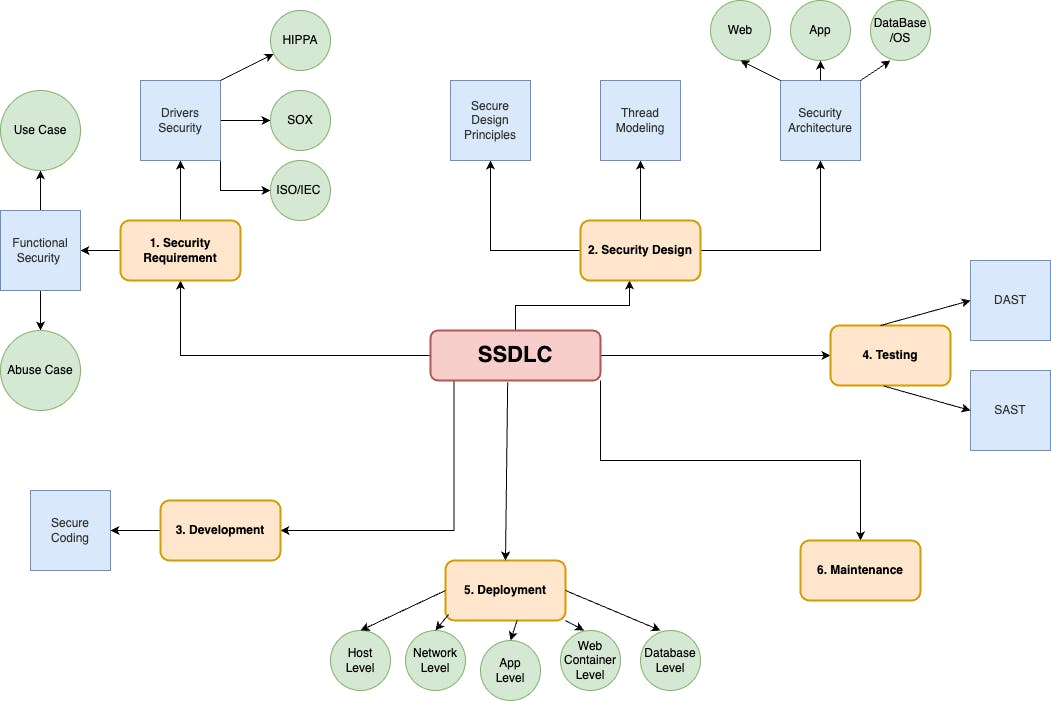
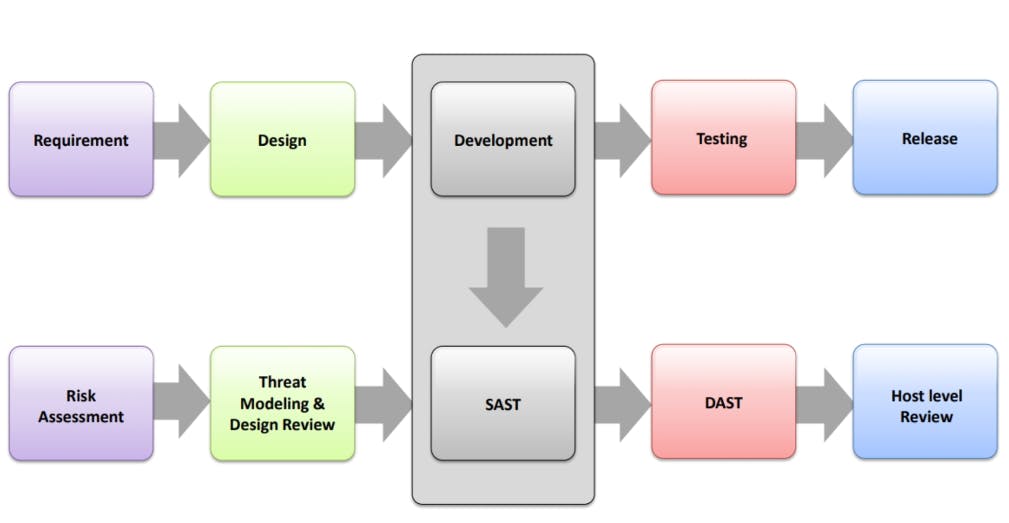
6 phases in secure software development:
I. Security Requirement
All requirements, including security, are highly specified in the first place and laid the groundwork for the rest phases. This module objectives focus functional security and Drivers security which need to be addressed to maintain the confidentiality, integrity and availability .
To gathering Security Requirement:
Eliciting software security requirements takes different approach
It should by enumerated separate from the functional requirement so they can be reviewed and tested
Mixing security requirement with functional requirement can make security requirement gathering process more complicated and inaccurate
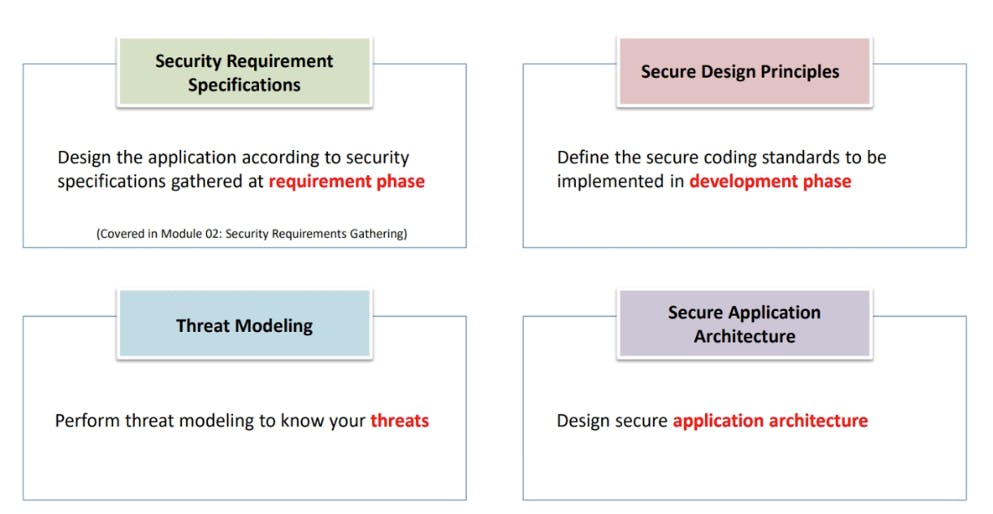
II. Security Design
“Most of the web applications are vulnerable due to insecure design of application at design phase”.
A security negligence at design and architecture phase may lead to vulnerabilities that are difficult to detect and expensive to fix in production. We must identifying the threats in sufficient details for developers to understand and code accordingly to mitigate the risk associated with the threat
Secure design actions:
III. Development
Secure coding is an essential aspect of the Software Development Life Cycle (SDLC) that focuses on building software applications with strong security measures in place. By following secure coding practices, you can significantly reduce vulnerabilities and protect your applications from potential cyber threats:
Input Validation
BAC
Injection Flaws
Improper error handling
Session management
Insecure storage
Cross-site scripting
DOS
Buffer overflows
Insecure configuration management
IV. Testing
Testing phase in SSDLC that is focussing investigation and discovery all vulnerabilities exist in application.
2 commons way:
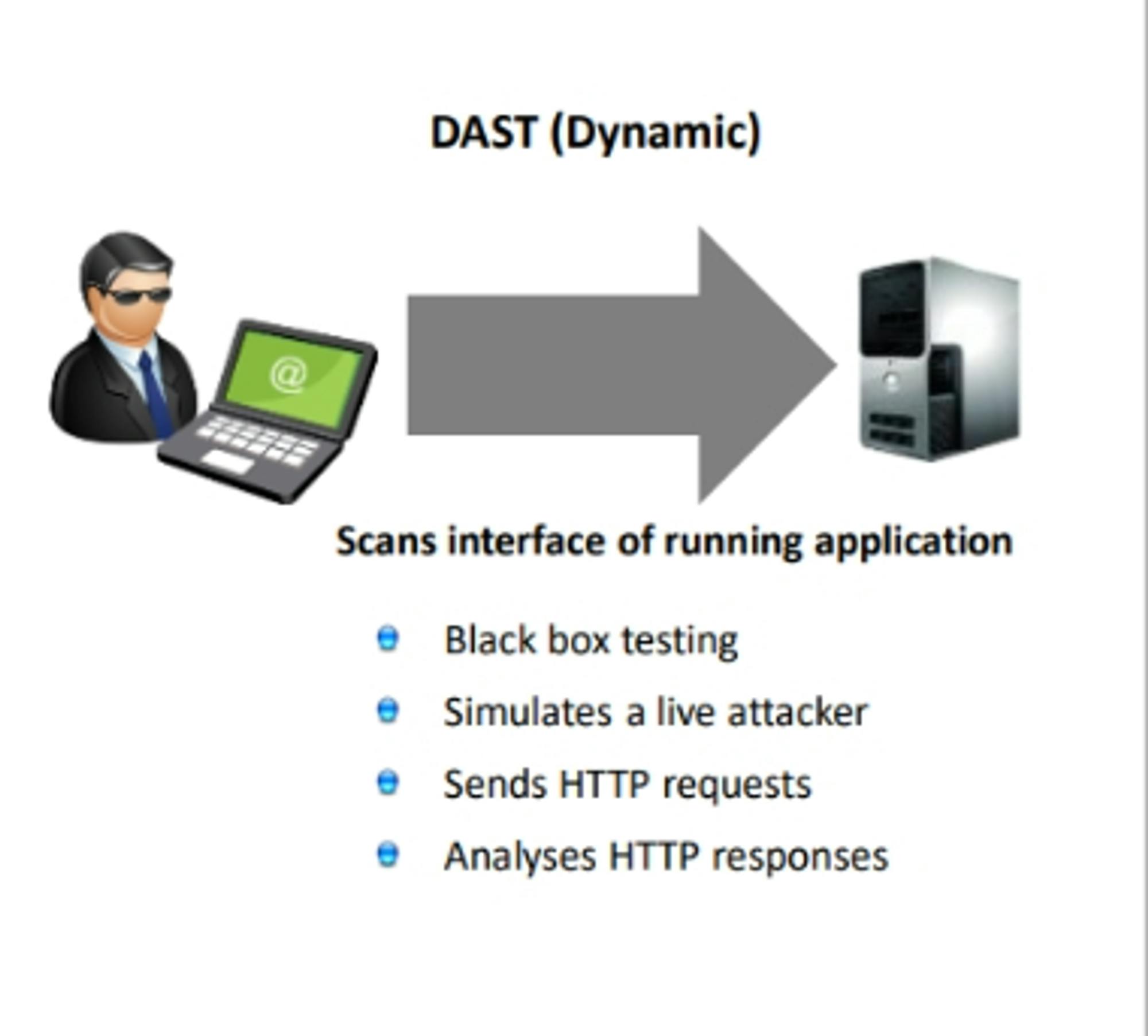
DAST: is a security testing technique which involves simulating attacks against the application and analyzes how the application behaves
SAST: Application Security Testing (SAST), or “white-box”, tools inspect source code or binaries and provide feedback on possible vulnerabilities. These tools are used during the development phase of the SDLC.
V. Deployment
Deployment is the last phase of SSDL where the application is moved from development environment to production environment
VI. Maintenance
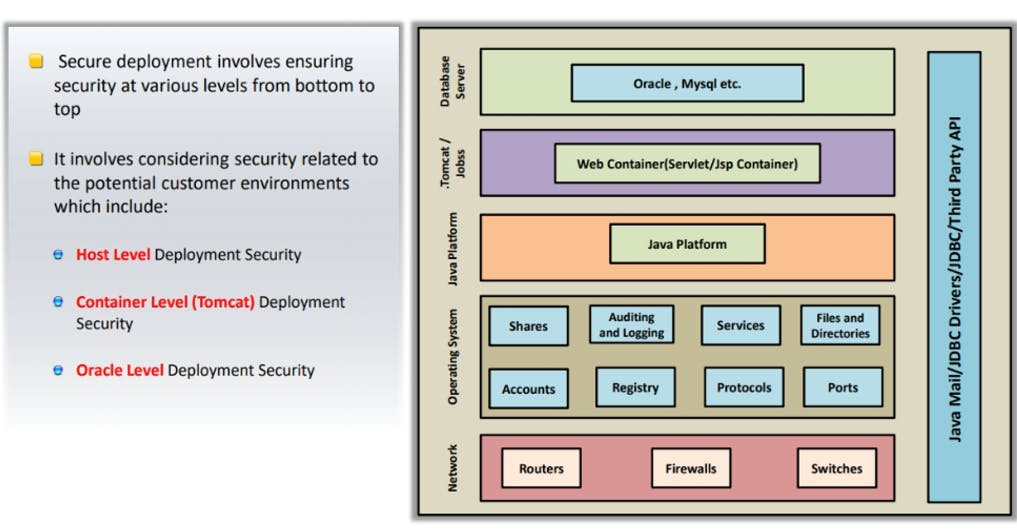
Security should be the critical consideration while deploying any application
JAVA web application secure deployment involves ensuring security at various levels from bottom to top
Administrator should ensure the physical security of a host machine, its OS security, and security of the all other software installed on the machine
A Web Application Firewall (WAF) provides a security layer that protects the web server from malicious traffic
Administrator should ensure secure setting of the web server (Apache Tomcat, Jboss(WildFly))
Administrator should configure and check the deployment security settings in both Server.xml and web.xml files carefully
Maintenance and monitoring is an iterative process undertaken after the initial deployment of the application